Fraud incidents: prevention using video-enabled document and identity management systems (Session 3/5)
6minFraud incidents: prevention using video-enabled document and identity management systems (Session 3/5)
In a world increasingly moving towards digital processes and staff located remotely, how do we reduce fraud and deception?
In this session we examine some fraud cases and explore how digital Smart Meeting enablement could have prevented problems.
| Learning Points: 1.Ways that fraud incidents may be prevented using smart tools 2.The behavioural benefits of video-assisted functionality 3. How the challenges of implementation can be overcome |
About this Session:
This session provides examples of fraud where transaction participants’ positive identification was not sufficient. It examines what affect Smart Meeting technologies would have in similar cases and explores the common barriers to solution implementation and how to overcome them.
“Smart Meeting technologies… stop fraudsters… and detect impersonation or misrepresentation with bone-fide customers”
Chris Jones, Managing Director, Icon UK Ltd
1. Fraud Examples
Two examples are given. The first is a mortgage fraud, which is also applicable to many other types of loan fraud. In online self-service transactions, organisations must counter the challenge of deception when organisations lose the ability to see the people involved. Even if they have the correct information from an accomplice, if a financial organisation does not operate with sufficient duty of care, it may find itself involved in a court claim with costs and reputational impact.
How can one be sure that an individual is who they say they are, without being able to verify that individual using visual, audio and behavioural insights from face-to-face in-person meetings?
The second more common example suggests that while a click-to-sign e-signature may be legal, if it does not require the signee to positively identify themselves with strong authentication for higher value transactions, in turn such inappropriate providence may again encourage future legal challenges.
When a dispute was taken to court, the e-signature (type your name) was insufficient evidence, as it could not be proved beyond doubt who actually signed the agreement.
2. How could these have been prevented by digital anti-fraud tools?
Using the Smart Meeting technologies discussed in the last MasterClass (#2), there are measures to both stop fraudsters signing up on the first place and detect impersonation or misrepresentation.
Smart Meeting methods enable the use of biometric face, voice or even signature recognition, with ID document validity checks and video recording of all parties within the same session. This video-assisted functionality offers a range of behavioural benefits in the fight against fraud due to:
• Fraudsters don’t want to be videoed
• The ability to conduct identity and credit reference checks on the fly
• Individual’s awareness of being recorded reduces their inclination to lie, exaggerate or mis-represent, both client and/or agent side
• Permanent records of the actual meeting and documents reviewed creates robust provenance.
3. What are the challenges of implementation and how can they be overcome?
It is not uncommon for organisations to have the technology they rely upon fragmented across their divisions, making it intimidating to build a platform to serve the customer across many integration points.
Regulators are also forcing changes to working practices: everyone has been affected in some way by GDPR data privacy rules and associated changes to operational procedures. Each industry and sector has specific and constantly evolving sets of requirements, so technologies need to be flexible and configurable to easily accommodate constant changes.
How can challenges be overcome?
There’s a long list remedies, mitigations and advice available, including:
• Pay attention to examining existing working practices to see if these are appropriate for Smart Meetings
• Look for an easy to use solution for both customers and your staff
• Build data privacy into your requirements and design
• Try to buy not build. For example, using solutions with pre-integrated connectors or low code approaches for connecting to your legacy applications will save time and be more reliable.
To build a case for change, an internal justification must be presented (often after gaining consensus) preferably including:
• Documenting the as-is baseline (also be used to measure future improvements against)
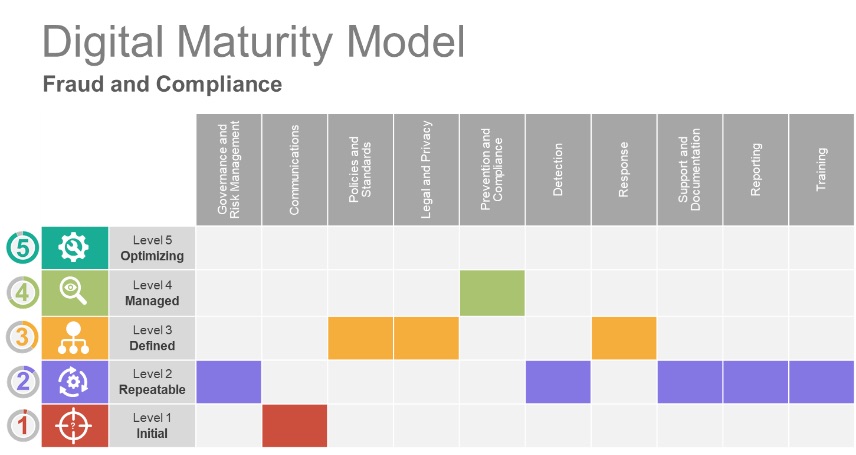
• Perform a digital maturity matrix assessment and compare the results to your peers
• Become more knowledgeable for the tools and platforms that are available
• Consider starting small, focusing on the biggest benefit or reduce fraud impacts the most
• Build a business case including a projected ROI model
• Get some external support by hiring a consultant to guide you through the process.
4. Why should I use external support?
Avoid the costs and delays of internal learning. External resources can help in many ways, ranging from consulting inputs to augmenting project teams, or actually leading the implementation from a business or technical perspective. Using external support can guide you through the process saving time and cost overall. Activities may include:
• Challenging current ways of working that conflict with current internal methodologies and/or user permissions
• Educating teams with the available options, selecting from broad experience to solve problem areas and highlighting the right tools for each specific organisation’s architecture
• Developing new shared visions and strategy, with documented output covering requirements and solution approach
| Take-aways:
1. Working Practice, Data Privacy and Platform challenges can be met flexibly 2. Smart Meeting tech stops fraudsters and enables bone-fide customer engagement 3. External specialist support helps build a case for change and optimise new processes |
Bonus
Interested in performing a Digital Maturity Matrix assessment now?
Click here to complete (<5 minutes).
Tip: check out the other videos for further free tools
Transform your and your Customer’s regulated Documents experience – ask how.
This transcript is also available as a PDF download within the files tab.
Icon UK – Fraud incidents: prevention using video-enabled document and identity management systems (Session 3/5)
Business Reporter asked Icon UK some probing questions concerning online fraud incidents and how to prevent them using video-enabled document and identity management systems.
In this session, we’re going to examine a couple of recent fraud cases. In a world increasingly moving towards digital processes and staff in remote offices, how do we reduce fraud and deception? We explore how digital smart meeting enablement could have prevented problems.
Fraud incident examples.
The first is a case of mortgage fraud, also applicable to many more types of loan in nature. When we lose the ability to see the people we’re dealing with, such as in an online remote self-service transaction, we open ourselves up to potential deception. Without being able to verify individuals using visual, audio, and behavioural insights for face-to-face in-person meetings, how can we be sure that they are who they say they are?
Take the example of banking customer who made a joint application to remortgage his house with his wife. His company was going through some financial problems, and he needed access to some cash. The mortgage application was completed online, and a follow-up call was made to the customer to confirm details.
After a short confirmation call, the application was approved, and funds were deposited in the customer’s account. The customer subsequently failed to make repayments on this mortgage, slipping into further debt until the bank decided to repossess his home.
The customer’s wife was surprised to find agents at her house and made a frantic call to the bank to find out for the first time that she was party to a new mortgage agreement. As it turned out, the customer had used his PA to pretend to be the wife during the confirmation call. The banker processed and accepted the application with little more than confirmation of the wife’s agreement.
A second type is more common. It’s a high-value contract executed online using simple e-signing tools, in this case, from a well-known US provider. However, this type of technology is often inappropriate providence for higher value transactions.
How could these incidents have been prevented by digital fraud prevention tools?
There are measures to stop fraudsters signing up in the first place and also to detect impersonation or misrepresentation throughout the years of engagement subsequently with bona fide customers. These include biometric face and voice recognition, identity document validity checks, and video recordings of all parties.
What are the main behavioural benefits of these video-assisted functionalities?
Fraudsters do not want to be videoed. The ability to conduct credit reference checks on the fly also reduces fraud. But the recording of individuals reduces their inclination to lie, exaggerate, or misrepresent, whether it’s client side or agent side. Having automated recording of all elements in an online meeting enables a full picture.
How can a business identify the solution that suits it best?
Identify and focus on the high impact areas first, pairing internal knowledge of the as-is process with an external understanding of best of breed options to create a new and clear desired future state plan. Find complete platforms that can be used flexibly for a spectrum of future use cases across the enterprise, whether that’s selling, onboarding, AML, KYC, compliance, advice service and support, or whatever.
What are the challenges of implementation, and how can they be overcome?
There’s a challenge of fragmentation of technology across organisation. Changing working practises and data privacy are major challenges also. They can be overcome by finding platforms for self-serve as well as human assisted processes; data privacy by design within fast integration using pre-integrated or connectors or low code approaches and for legacy applications; and easy-to-use systems and attention to working practises, such as a professionally suitable environment within call centres as a backdrop to video.
What are the biggest issues that hold businesses back from grasping these processes?
It comes down to internal knowledge, external support, and tools or platform choice. Not all transactions have the same value nor risk and consequences. Solution flexibility’s key. External specialist support, such as from ourselves, helps here.
We work with customers with high demands. And we aim to anticipate and respond to an ever-changing set of explicit and latent requirements. Challenging the current ways of working works well, working smarter, not just the same faster. And that means providing educating on the options, guiding from experience to solve problems and highlighting the right tools to compliantly simplify the complex.
Hands-on experience with a range of advanced tools enables new visions of the big picture to be created. With well-designed, highly configurable yet standardised technologies to support digital automation initiatives, process mapping does not need to constrain happy customer journeys.
In the next session, we’ll discuss how anti-fraud capabilities can drive conversion rates and customer retention, thus improve the ROI of deployment.
-
Icon UK - Fraud incidents: prevention using video-enabled document and identity management systems (Session 3/5)
You must Login to access notes.
About the expert

Icon UK
Icon UK works with clients to unlock step-change cost reductions and business benefits from their Enterprise Document Management Infrastructure.
See more from Icon UK Visit icon-uk.net/index.htmlAll videos in this course
Lessons
- Log in to get access Online fraud types in high value transactions: are we doing enough to prevent it? (Session 1/5) 7min
- Log in to get access Solutions and Capabilities to prevent digital fraud (Session 2/5) 7min
- Log in to get access Fraud incidents: prevention using video-enabled document and identity management systems (Session 3/5) 6min
- Log in to get access The positive impact of platforms on conversion and retention rates (Session 4/5) 5min
- Log in to get access MasterClass Series Summary 2min